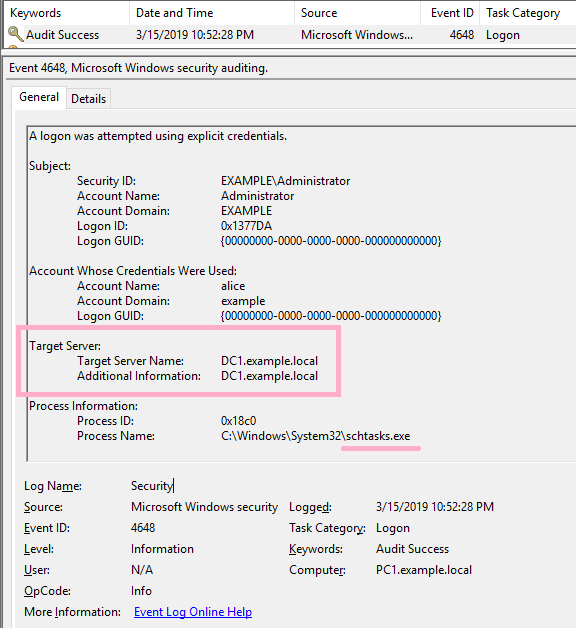
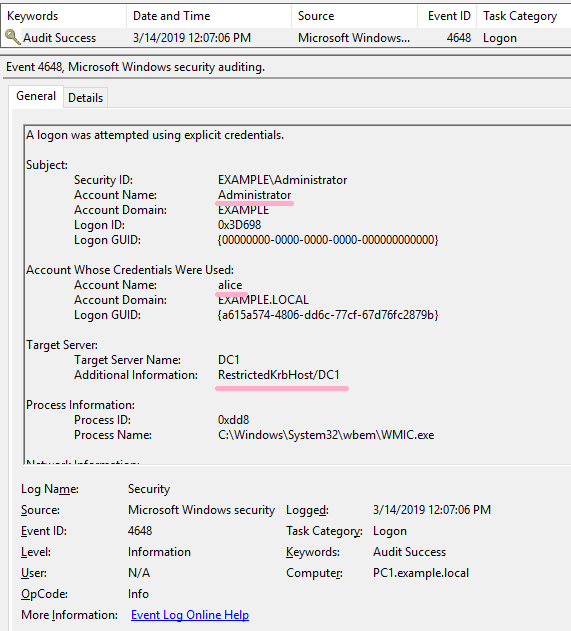
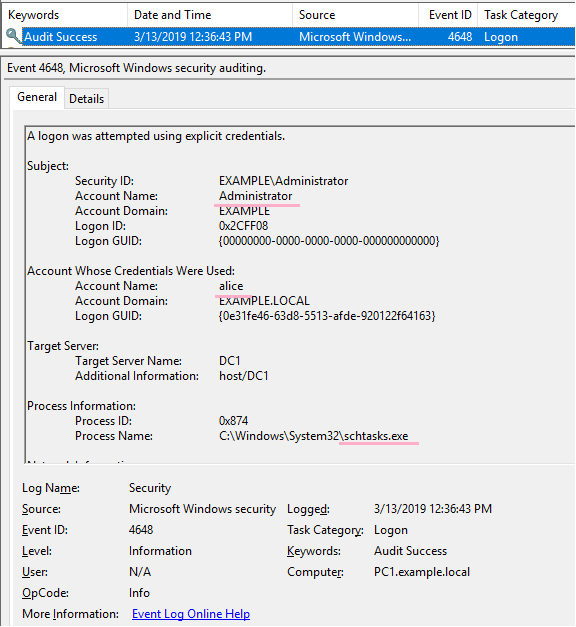
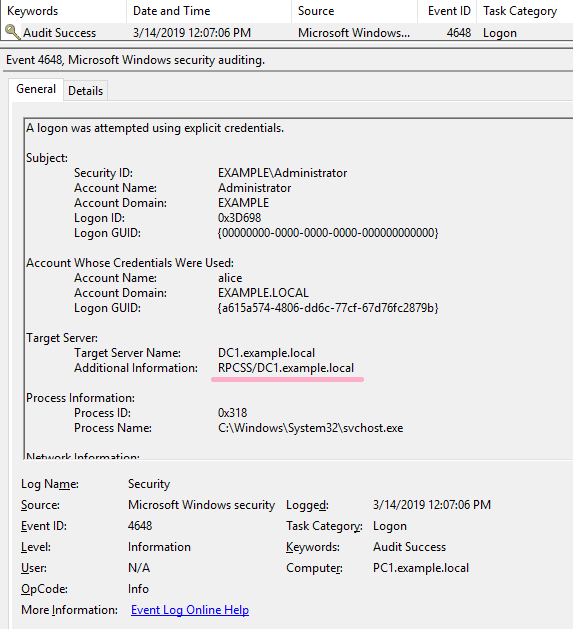
MENASEC - Applied Security Research: An overview of Windows EventID 4648 - Logon with explicit credentials

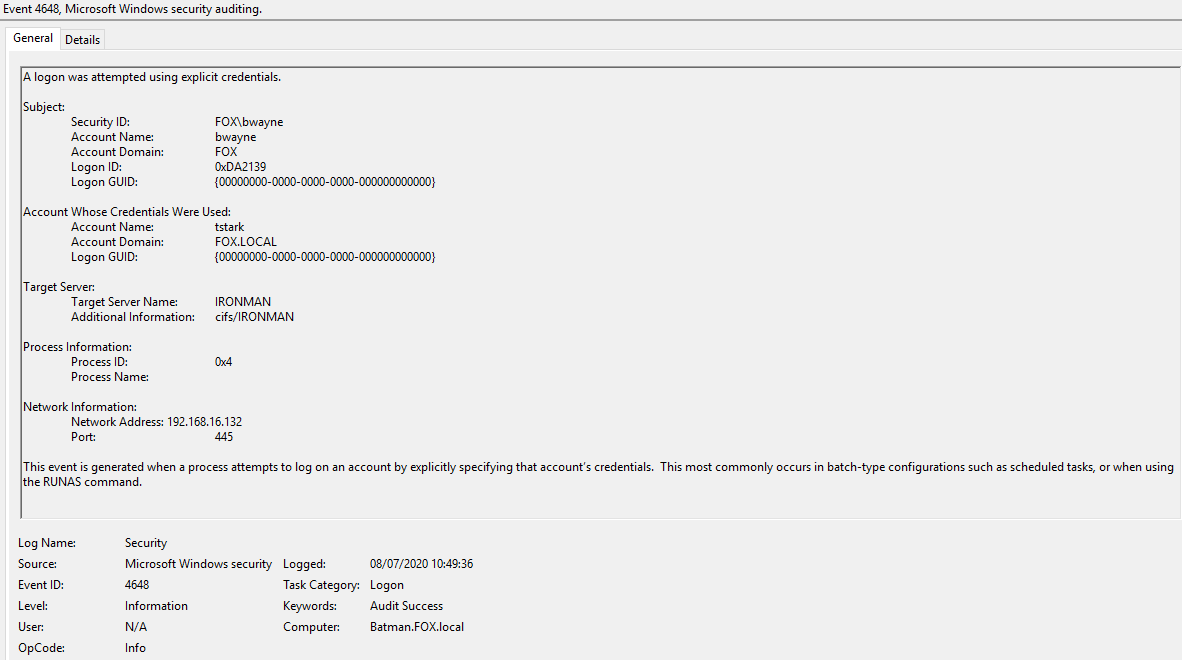
Windows event ID 4648 - A logon was attempted using explicit credentials | Windows security encyclopedia
Continuous windows events are generated in the windows system logs while installing Horizon Composer Server (84204) | VMware KB

Detecting Lateral Movement 101 (Part-2): Hunting for malcode Execution via WMI using Windows Event Log Analysis | by imp hash | Medium
MENASEC - Applied Security Research: An overview of Windows EventID 4648 - Logon with explicit credentials

MENASEC - Applied Security Research: An overview of Windows EventID 4648 - Logon with explicit credentials

AppInsight for Active Directory Alert is not really helpful ? - Forum - Server & Application Monitor (SAM) - THWACK
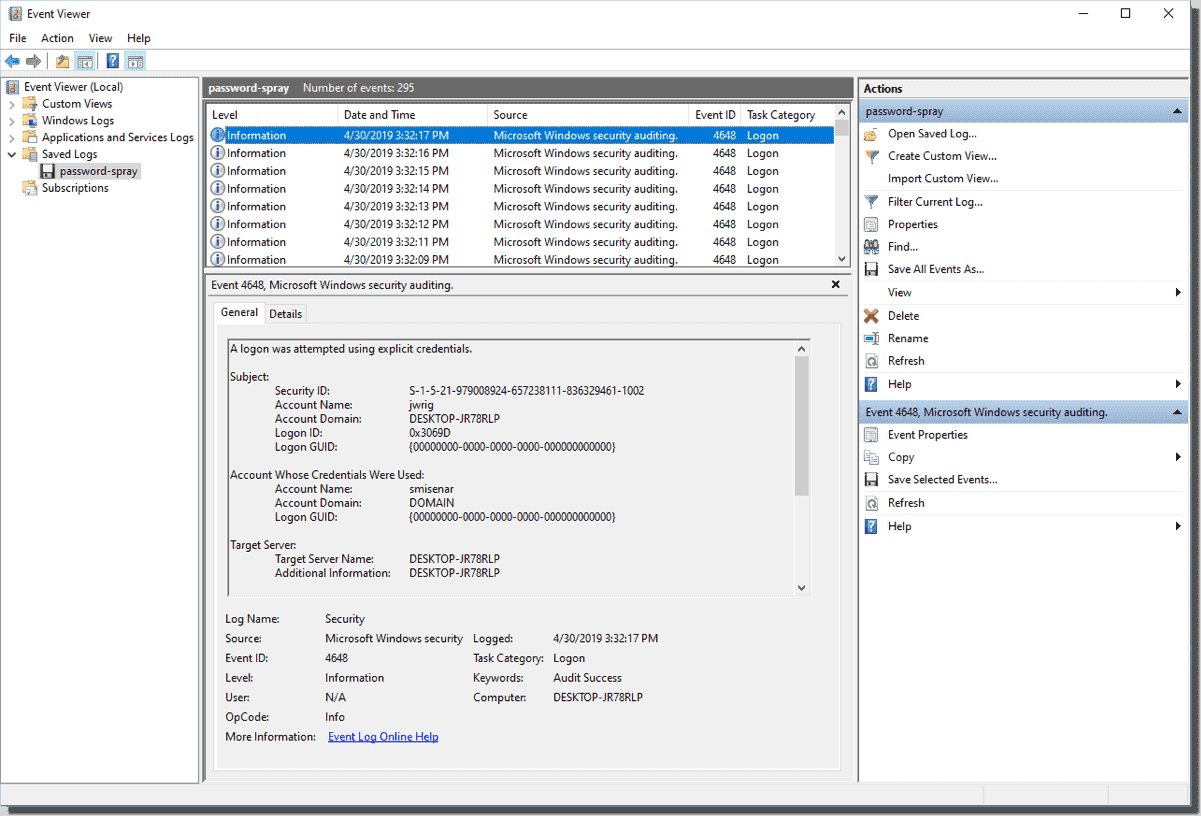
![4648: A Logon was Attempted Using Explicit Credentials [Fix] 4648: A Logon was Attempted Using Explicit Credentials [Fix]](https://cdn.windowsreport.com/wp-content/uploads/2022/12/Untitled-design-22-1200x1200.png)
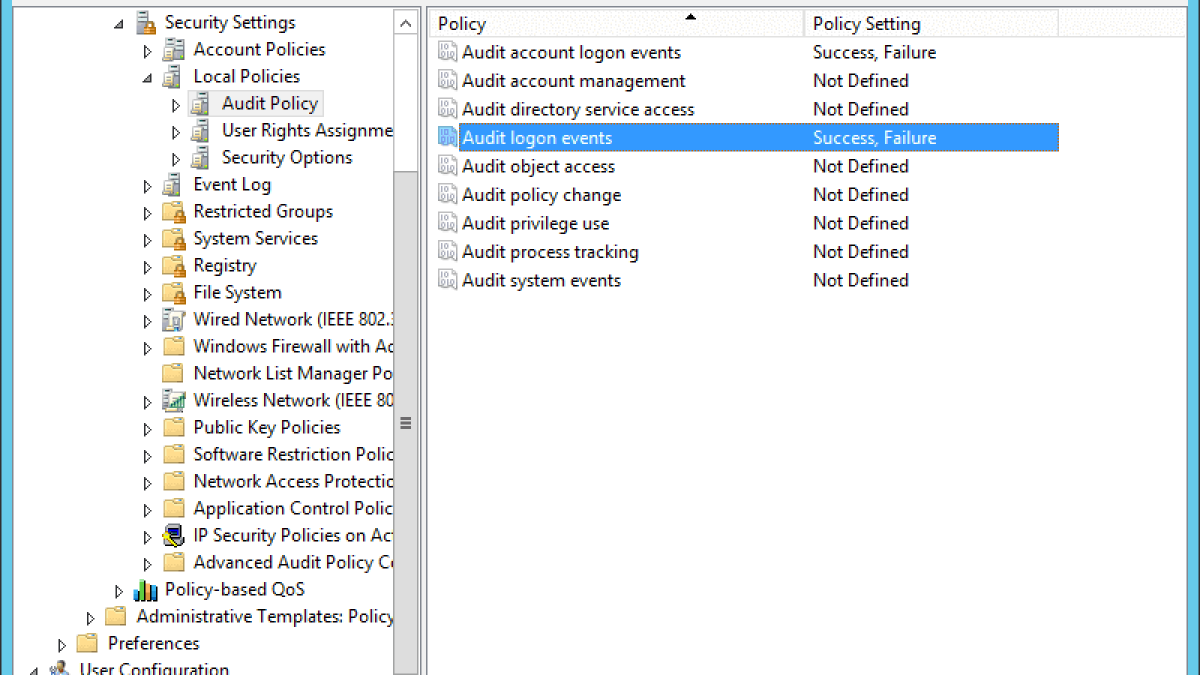


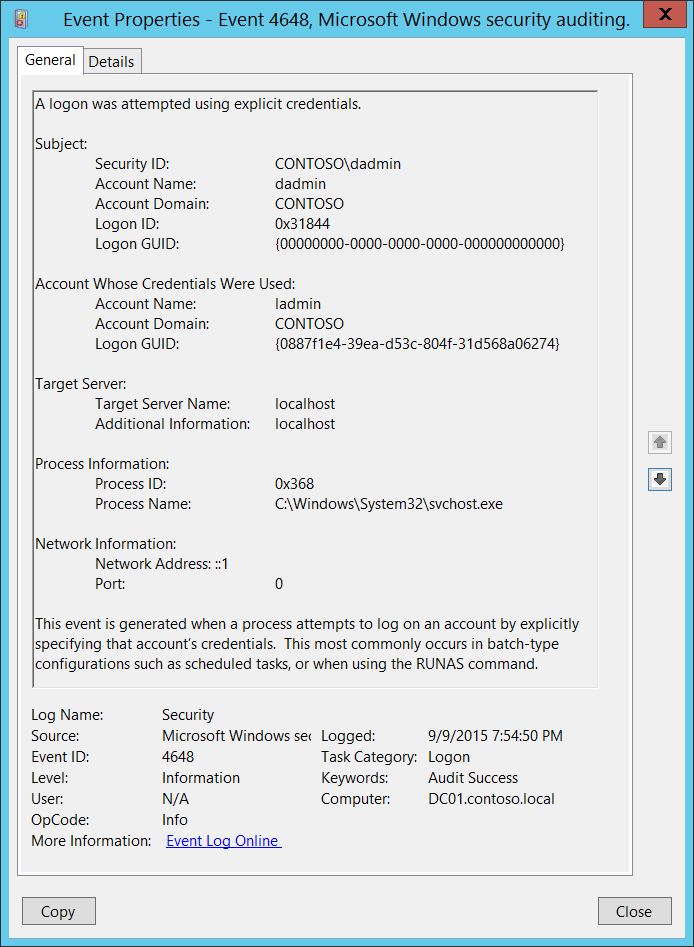
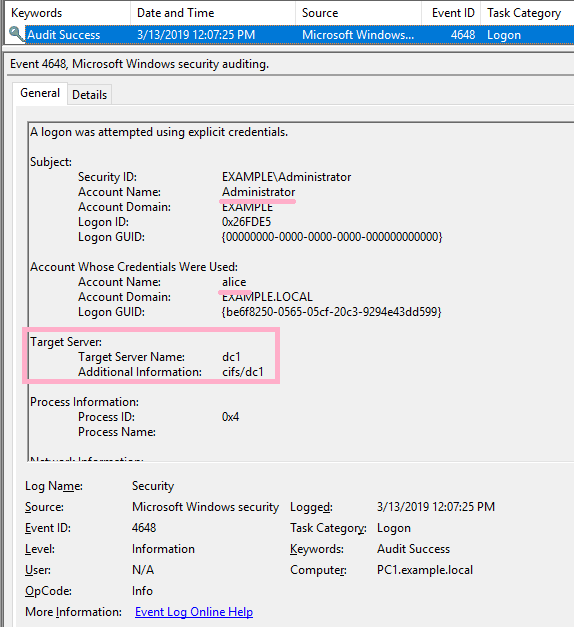




![4648: A Logon was Attempted Using Explicit Credentials [Fix] 4648: A Logon was Attempted Using Explicit Credentials [Fix]](https://cdn.windowsreport.com/wp-content/uploads/2022/12/Untitled-design-22.png)